Authors of this chapter: Mario and Donny from Beosin research team

According to Beosin Alert monitoring and early warning, the total losses in the Web3 field due to hacker attacks, phishing scams and project party Rug Pull in the first quarter of 2024 reached 778 million US dollars. Among them, there were 39 major attack incidents with a total loss of approximately 617 million US dollars; 43 project party Rug Pull incidents with a total loss of approximately 75.5 million US dollars; the total loss of phishing scams was approximately 86.24 million US dollars.

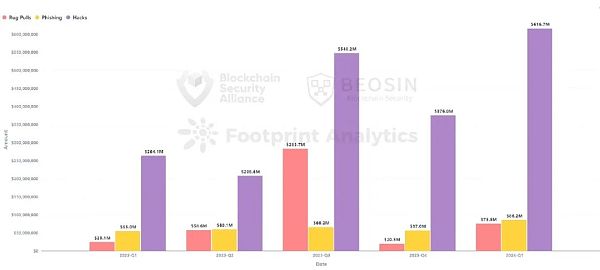
The total loss in the first quarter of 2024 was approximately US$778 million, an increase of approximately 126% year-on-year and approximately 72% month-on-month. The loss amount from hacker attacks was higher than any quarter in 2023.
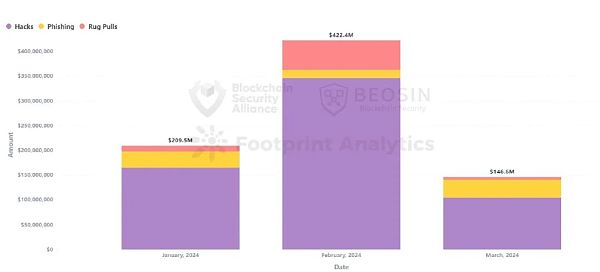
The total loss amount in February reached US$422 million, the month with the highest loss amount in the first quarter of 2024.
From the perspective of the types of projects attacked, the gaming platform has become the project type with the highest amount of losses for the first time. Six attacks on Web3 gaming platforms have caused a total loss of $365 million, accounting for 59% of all attack losses.
From the perspective of the amount of losses on each chain, Ethereum is still the chain with the highest amount of losses and the most attacks. 18 attacks on Ethereum caused a loss of $342 million, accounting for 55.4% of the total losses.
From the perspective of attack methods, there were 13 private key leaks this quarter, causing losses of $458 million, accounting for 74.3% of the total attack losses, which is the highest proportion of attack types.
From the perspective of capital flow, most of the stolen assets were frozen and recovered this quarter. About $303 million (49.2%) of the stolen funds were frozen, and $79.45 million (12.9%) of the stolen funds were recovered.
From the perspective of audits, the proportion of audited projects among the attacked projects has increased.

39 major attacks caused a total loss of $616.7 billion
In the first quarter of 2024, Beosin Alert monitored 39 major attacks in the Web3 field, with a total loss of $616.7 billion. Among them, there were 2 security incidents with a loss of more than $100 million, 5 incidents with a loss of $100 million to $100 million, and 21 incidents with a loss of $1 million to $10 million.
Attacks with losses exceeding 10 million US dollars (sorted by amount):
● PlayDapp - $290 million
Attack method: private key leakage Chain platform: Ethereum
On February 9, the blockchain game platform PlayDapp was attacked, and the hacker's address minted 200 million PLA tokens worth $36.5 million. After PlayDapp failed to negotiate with the hacker, the hacker minted another 1.59 billion PLA tokens worth $253.9 million on February 12, and sent part of the funds to the Gate.io exchange. Afterwards, the project suspended the PLA contract and migrated the PLA tokens to PDA tokens.
● Chris Larsen (Ripple co-founder) - $112 million
Attack method: private key leakage Chain platform: XRP
On January 31, Ripple co-founder Chris Larsen said that his four wallets were hacked and a total of about $112 million was stolen. The Binance team has successfully frozen $4.2 million worth of XRP stolen by the attacker.
● Munchables - 62.3 million dollars
Attack method: social engineering Chain platform: Blast
On March 26, Munchables, a Web3 game platform based on Blast, was attacked and lost about 62.5 million dollars. It is suspected that the project was attacked because it hired North Korean hackers as developers. All the stolen funds have been returned by the hackers afterwards.
●FixedFloat - $26.1 million
Attack method: security structure vulnerability Chain platform: Ethereum
On February 17, the crypto exchange FixedFloat was attacked and lost about $26.1 million. The hacker has transferred most of the stolen funds to the eXch exchange. On February 20, FixedFloat stated that the attack "was not committed by our employees, but an external attack caused by a vulnerability in our security structure."
●Curio Ecosystem - $16 million
Attack method: Contract vulnerability - Access control vulnerability Chain platform: Ethereum
On March 23, the RWA infrastructure Curio Ecosystem was attacked, causing losses of approximately $16 million.
●Somesing-11.58 million US dollars
Attack method: private key leakage Chain platform: Klaytn
On January 27, South Korea's Web3 social music service was attacked and lost 730 million native tokens SSX, worth 11.58 million US dollars.
● Jihoz.ron (Ronin co-founder) - 10 million US dollars
Attack method: private key leakage Chain platform: Ronin
On February 23, the two addresses of Ronin co-founder jihoz.ron lost approximately 10 million US dollars due to private key leakage.

Game platforms became the project type with the highest loss for the first time
This quarter, the project type with the highest loss was the game platform. Six attacks on Web3 game platforms caused a total loss of $365 million, accounting for 59% of all attack losses. For the first time, the game platform became the type of project with the highest loss.
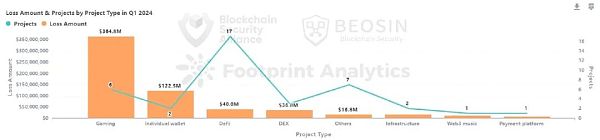
The second-ranked victim type was personal wallets. Two personal wallet thefts caused a loss of $122.5 million. Both personal wallet thefts were from co-founders of well-known projects (Ripple and Ronin).
Of the 39 hacker attacks, 17 occurred in the DeFi field, accounting for about 43.6%. These 17 DeFi attacks resulted in a total loss of $39.96 million, ranking third among all project types.
Other attacked project types include: DEX, infrastructure, payment platform, Web3 music platform, etc.

Ethereum is the chain with the highest loss and the most attacks
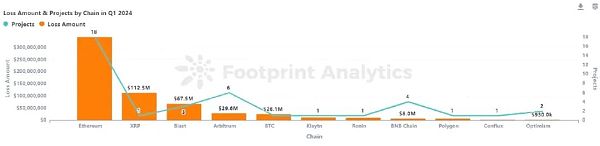
Similar to 2023, Ethereum is still the public chain with the highest loss. 18 attacks on Ethereum caused a loss of US$342 million, accounting for 55.4% of the total losses.
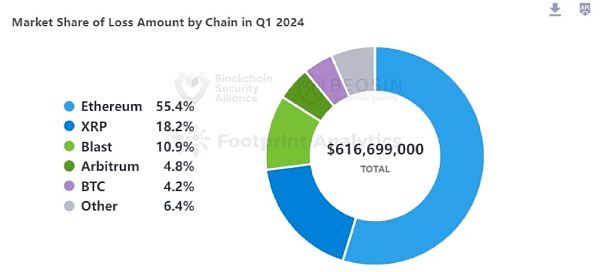
The second largest public chain in terms of loss is XRP, which came from a theft of the wallet of Chris Larsen, co-founder of Ripple.
The third largest public chain in terms of loss is Blast. Three attacks on the Blast chain caused a total loss of $67.5 million. Blast chain ranks first in terms of loss among major emerging public chains.
This quarter, BNB Chain only had 4 major security incidents, with a loss of approximately $8.01 million. The ranking of both the amount of loss and the number of incidents has dropped significantly compared to 2023.

74.3% of the losses came from private key leaks
There were 13 private key leaks this quarter, causing losses of $458 million, accounting for 74.3% of the total attack losses. As in 2023, the losses caused by private key leaks are still the first among all attack types. The private key leaks that caused large losses include: PlayDapp ($290 million), Ripple co-founder Chris Larsen ($112 million), Somesing ($11.58 million), and Ronin co-founder Jihoz.ron ($10 million).

Of the 39 attacks, 21 were from contract vulnerability exploits, with a total loss of $65.56 million, ranking second.
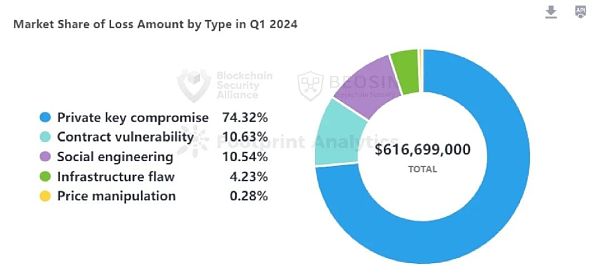
The third-ranked attack method in terms of loss amount was social engineering attacks, with three social engineering attacks causing losses of approximately $65 million.
By breaking down the vulnerabilities, the top three vulnerabilities causing losses were: algorithm flaws (US$22.78 million), access control vulnerabilities (US$16.32 million), and business logic vulnerabilities (US$11.28 million). The most common vulnerabilities were business logic vulnerabilities, with 7 of the 21 contract vulnerability attacks being business logic vulnerabilities.

Atom Asset (AAX) Evades Anti-Money Laundering (AML) Analysis
Recently, Atom Asset (AAX), a defunct Hong Kong exchange, began moving funds from its wallets to various decentralized exchanges and centralized platforms, allegedly to evade anti-money laundering (AML) controls. Before being discovered, the last known transactions involving AAX exchange wallets occurred in October 2023 and November 2022. Before its collapse, AAX was one of the largest cryptocurrency exchanges in Hong Kong, with more than 2 million users.
According to the analysis of the Beosin team, it was found that since January 29, 2024, AAX exchange has begun to transfer 25,100 ETH from its exchange wallet. The transferred funds were divided into three transactions, one for 500 ETH, one for 600 ETH, and one for 24,000 ETH. The transferred funds are converted to more than 74 million US dollars based on the current price.
The ins and outs of the AAX exchange incident
On November 13, 2022, just two days after the cryptocurrency exchange FTX filed for bankruptcy, AAX also stopped withdrawals and cleared all social channels due to counterparty risk exposure. Initially, AAX attributed the freeze to security measures against suspected malicious attacks.
On November 15, 2022, the AAX exchange issued a statement saying that its platform needed maintenance, and in addition to suspending withdrawals, derivatives would be automatically liquidated. Since then, AAX has stopped platform operations and social media updates. The strange thing is that after 426 days of silence, the AAX exchange wallet started to move, and large amounts of funds began to be transferred to other addresses, trying to avoid the identification and monitoring of AML tools!
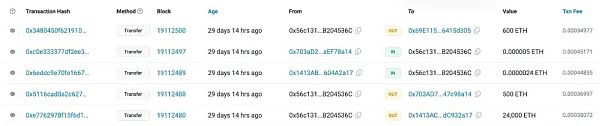
link: https://etherscan.io/address/0x56c1319b31a5316a327bd889d58c8633b204536c
Analysis of funds on the AAX exchange event chain
Beosin KYT anti-money laundering analysis platform conducted an in-depth study of the recent on-chain activities of the AAX exchange wallet and found a series of risky activities. First, all 25,100 ETH have been transferred, and the operators have taken various measures to convert part of the ETH into USDT, and then transferred the funds to different blockchains through the cross-chain bridge to launder the funds.
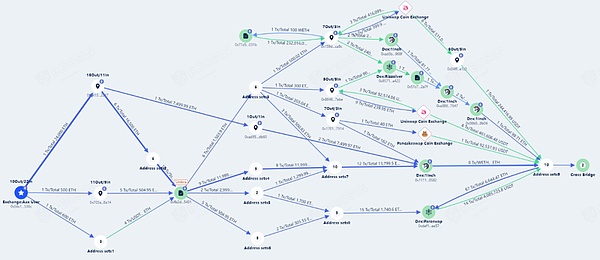
Beosin KYT Anti-Money Laundering Platform
Among them, most of the funds were transferred to the Tron blockchain and transferred through some addresses, and then deposited in certain addresses without being transferred. This behavior shows an obvious attempt to evade AML and try to conceal the true source and destination of the funds.
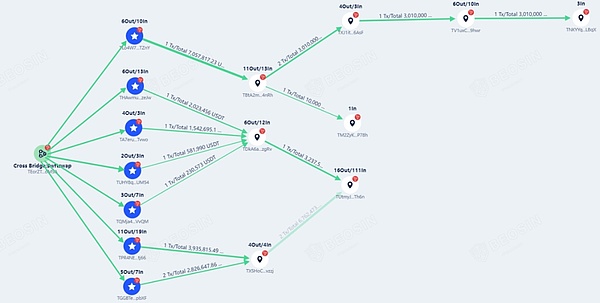
Beosin KYT Anti-Money Laundering Platform
The Hong Kong police took swift action against the fraudulent activities and arrested two people related to AAX. They are currently working to map the path of the transfer of funds and recover the assets of affected users.
The AAX exchange uses technical means such as decentralized exchanges, cryptocurrency exchanges, and cross-chain bridges to try to obscure the path and source of capital flows. This poses a huge challenge to regulators and AML analysis platforms.

Most of the stolen assets were frozen and recovered
According to the analysis of Beosin KYT anti-money laundering platform, of the stolen funds in the first quarter of 2024, about $303 million (49.2%) of the stolen funds were frozen, and $79.45 million (12.9%) of the stolen funds were recovered. This proportion is much higher than in 2023.
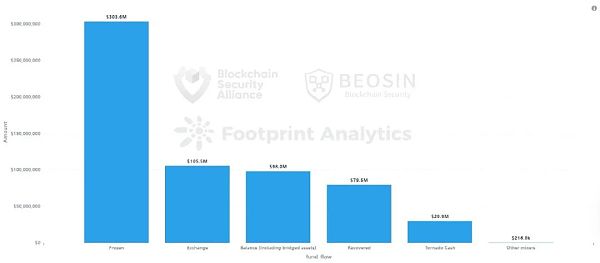
About $105.5 million of the stolen funds were transferred to various exchanges, accounting for about 17.1%. Compared with 2023, the proportion of stolen funds transferred by hackers to exchanges has increased significantly this year. This puts higher requirements on exchanges for anti-money laundering and compliance.
A total of $30.12 million (4.9%) was transferred to mixers: $29.9 million was transferred to Tornado Cash; $216,000 was transferred to other mixers. Compared with last year, the amount of stolen funds cleaned through mixers in the first quarter of 2024 decreased significantly.

The proportion of audited project parties has increased
Of the 39 attacks, 12 of the project parties were not audited, and 24 of the project parties were audited. The proportion of audited projects is slightly higher than that in 2023, which shows that the entire Web3 industry project has paid more attention to security.
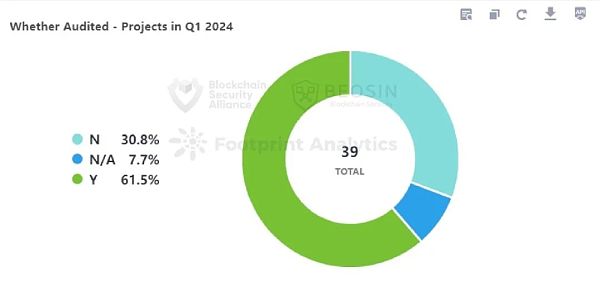
Of the 12 unaudited projects, 8 (66.7%) were contract vulnerability incidents. In contrast, 13 (54.2%) of the 24 audited projects had contract vulnerability incidents. This shows that auditing can improve the security of projects to a certain extent.

43 Rug Pull events with a total loss of US$75.5 million
In the first quarter of 2024, a total of 43 Rug Pull events were monitored, involving a total amount of US$75.5 million.
The top five Rug pull events in terms of loss amount are: Bitforex (US$56.5 million), Hector Network (US$2.7 million), MangoFarm (US$2 million), OrdiZK (US$1.4 million), and RiskOnBlast (US$1.3 million). These 5 Rug Pull incidents were distributed in four chains: Ethereum, Fantom, Solana, and Blast.
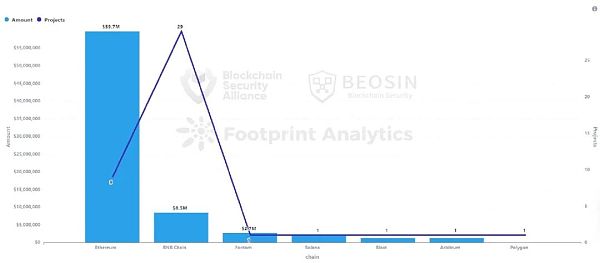
The total amount of Rug Pull on the Ethereum chain reached 59.68 million US dollars, accounting for 79% of the total losses. The most Rug Pull incidents occurred on the BNB Chain, with a total of 29 times, accounting for 67.4% of the total number of incidents.

Compared with the previous quarter, the total losses caused by hacker attacks, phishing scams, and project Rug Pulls in the first quarter of 2024 increased significantly, reaching 778 million US dollars. The rise in coin prices this quarter has a certain impact on the increase in the total amount, but overall, the situation in the Web3 security field is still not optimistic.
The most harmful attack type this quarter is private key leakage, about 74.3% of the loss amount comes from private key leakage incidents, which is consistent with the data in 2023. From the perspective of project type, private key leakage incidents are spread across all areas of Web3: game platforms, DeFi, personal wallets, infrastructure, NFT, payment platforms, gambling platforms, data storage platforms, etc. Each Web3 project party/individual user needs to be vigilant, store private keys offline, use multi-signatures, use third-party services with caution, and conduct regular security training for privileged employees.
Most assets were frozen and recovered this quarter, which marks the improvement of the global regulatory system and the strengthening of anti-money laundering efforts. This quarter, the proportion of stolen funds transferred by hackers to exchanges has also increased significantly, which requires exchanges to identify hacker behavior in a timely manner and actively cooperate with law enforcement agencies and project parties to freeze funds and conduct evidence collection. Currently, the cooperation between exchanges and law enforcement agencies, project parties, and security teams has achieved relatively obvious results. I believe that more stolen funds will be recovered in the future.
Of the 39 attacks this quarter, 21 still came from contract vulnerability exploits. It is recommended that project parties seek audits from professional security companies before going online.
 JinseFinance
JinseFinance





























