In 2025, Web3 will enter a new phase of "larger-scale and higher-frequency use," and wallets will rapidly evolve from "crypto storage tools" to on-chain entry points and transaction operating systems. Market research firm Fortune Business Insights predicts that the crypto wallet market will be worth approximately $12.2 billion in 2025 and could grow to $98.57 billion by 2034. The expansion on the user side is equally significant: a16z crypto estimates in its "State of Crypto 2025" report that there are approximately 40-70 million active crypto users, while the number of crypto asset holders who "hold crypto but are not necessarily active on-chain" is approximately 716 million; a report by Crypto.com Research also gives a figure that the number of global crypto holders increased from 681 million to 708 million in the first half of 2025. The rise in scale and penetration has also amplified security risks. It's no longer just about whether contracts have vulnerabilities, but whether risks can be prevented at key user points, such as clicking links, connecting wallets, signing authorizations, and transferring funds. The "attack surface" in the blockchain world often extends beyond contract vulnerabilities, frequently involving low-barrier phishing, fake domains, impersonating customer service, and authorization fraud – all pre-transaction risks. For example, Chainalysis's definition of "crypto drainers" (wallet drainers/phishing authorization tools) points out that these tools don't steal account passwords, but rather induce users to connect their wallets and approve malicious transactions, thereby directly transferring assets. Public data also shows that losses related to "wallet drainers" approached $500 million in 2024. Therefore, improving the security of Web3 wallets will no longer focus solely on whether contracts have vulnerabilities, but will require further attention to how to proactively intercept risks at key points in user behavior, i.e., "pre-transaction security." In this industry context, "security" is increasingly difficult to address with a mere slogan; instead, it's more like a set of governance capabilities that need continuous proof: **Verifiability, traceability, and timely disclosure** are becoming crucial criteria for users choosing a wallet. From "Security Claims" to "Understandable Security Capabilities Lists" For a long time, wallet projects discussing security commonly used phrases like "We've conducted audits," "We have white papers," and "We value risk control." However, with the industrialization of fraud and phishing, these "security claims" are losing their persuasiveness. The moment a user truly suffers a loss often occurs within extremely brief interactions such as clicking a link, connecting a wallet, and signing an authorization. Chainalysis describes "crypto drainers" as a typical path: attackers impersonate legitimate pages, guiding users to complete authorizations, and then the assets are transferred away; their research even mentions cases of forging Magic Eden pages to carry out malicious transactions targeting Ordinals users. Public data is also driving the industry narrative towards "understandability." Security Week, citing statistics from Scam Sniffer, states that in 2024, losses caused by wallet drainers approached $500 million, with over 332,000 victims—these incidents do not require attackers to break through complex systems, but rather rely more on users "not understanding the risks" during the interaction. On the other hand, Chainalysis also estimated in its 2025 disclosure that on-chain fraud revenue in 2024 was at least $9.9 billion, and this figure may be revised upwards as more addresses are identified. When the risk primarily stems from "readability gaps on the user side," wallet vendors must move security from backend engineering to the frontend of communication. As a result, more and more wallets in the industry are beginning to "productize" their security capabilities: instead of simply telling you "we are secure," they break down protective actions into a list that users can understand—which tokens will be marked as high-risk, which transactions will trigger alerts, which addresses or DApps will be blocked, and why. The essence of this change is to rewrite security from a "qualification narrative" to an "interaction narrative": allowing users to obtain actionable information before signing, rather than having to review an audit PDF afterward. Under this trend, OKX Wallet's newly launched and upgraded Security Center page provides a typical example of this "list-based expression." The page clearly outlines user-facing security capabilities as three "front lines of defense": Token risk detection, Transaction monitoring, and Address screening, explaining their function in a single sentence, such as "marking high-risk tokens to reduce exposure to honeypots and malicious parties," "real-time cross-chain monitoring to identify suspicious on-chain activity," and "blocking interactions with malicious DApps and addresses." The advantage of this approach is that even if users don't understand security terminology, they can quickly understand their current actions—should I click, sign, or transfer now?
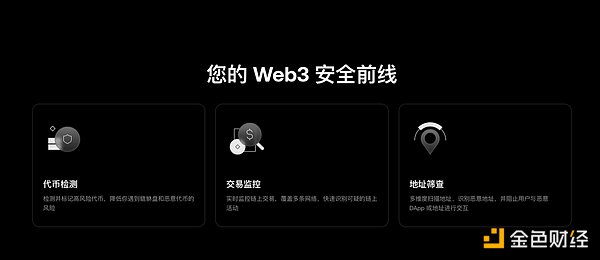
Click here for: OKX Wallet Security Landing Page Audit Report: https://web3.okx.com/zh-hans/security
More importantly, "understandable" does not equal "self-serving".
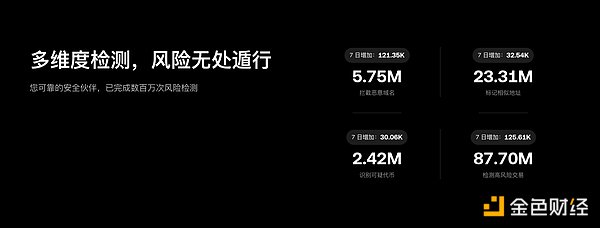
Audit Information“Publicly Verifiable”: Transforming third-party endorsements from“Linked”to“Verifiable Chain of Evidence”
 Weatherly
Weatherly





